PII Data Encryption (OTP)
Existing Flow
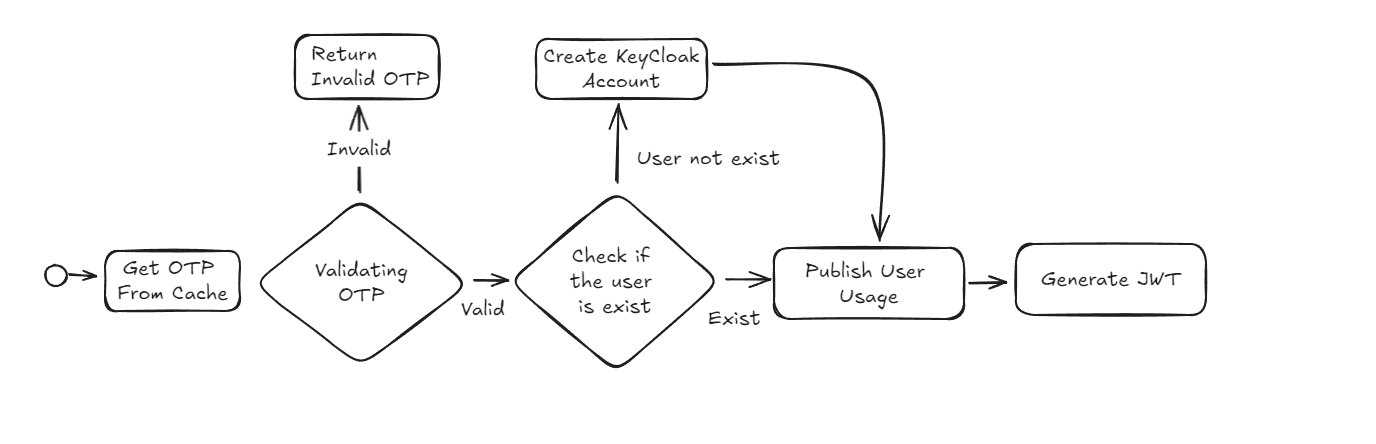
Currently, we collect the Authentication usage from API /otp/validate and to create the user’s Keycloak account in this API, and then publish the usage to Google Pub/sub. The flow is as follows:
Since we are planning to implement the ISO, we need encapsulate user's PII data in the OTP validation process. The flow is as follows:
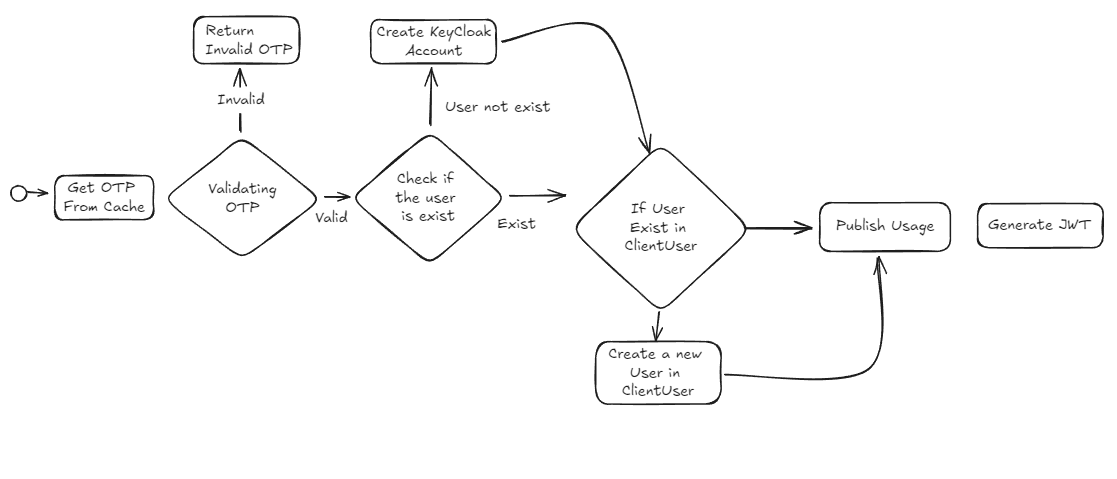
Thus, we will store the C-UID inside the table, and we will communicate and encrypt user information by using the c_uid field. Therefore, we need some changes in the API Contract as well, instead of only sending the phone number or email of the user, we need to send the c_uid as well.
So the API request in /otp/validate will be changed because we need to send the c_uid as well.
Existing API Contract
POST {{BASE_URL}}/v2/:realm_id/otp/validate
{
"client_id": "{{CLIENT_ID}}",
"client_secret_key": "{{CLIENT_SECRET_KEY}}",
"user_id": "{{USER_ID}}",
"otp": "{{OTP}}"
}
New API Contract
POST {{BASE_URL}}/v2/:realm_id/otp/validate
{
"client_id": "{{CLIENT_ID}}",
"client_secret_key": "{{CLIENT_SECRET_KEY}}",
"user_id": "{{USER_ID}}",
"otp": "{{OTP}}",
"c_uid": "{{C_UID}}"
}
The API will be responsible for encrypting the user's PII data and storing it in the database. The encryption process will be done by the API itself, and the API will be responsible for decrypting the data as well. The encryption and decryption process will be done using the c_uid field.